Security 8 - New EMV Cards
EMV cards are about to be rolled out massively in the US, so you heard it here first!
EMV Card - aka Chip Card
- EMV (Europay Mastercard Visa) have been in use in Europe for over 20 years (EMV on wikipedia)
- Known as "Chip and Pin" or "Chip and Signature" cards
- There are various attacks to nibble at EMV
- However EMV is much more secure than old mag-stripe
- The details are complicated, but the basics are simple
How Do Mag-Stripe Credit Cards Work?
- The old way - really quite insecure
- One "secret" is the Credit Card number, printed on the front of the card
- There's also a "CVV1" number on the mag stripe, not printed on the back
- Anyone who has these "secrets" can try making charges
- There is a different CVV2 number printed on the back
- Card-swipe: "secret" is the CC number + CVV1
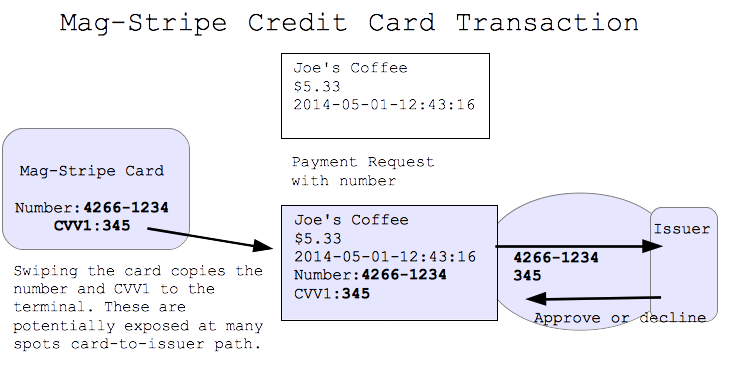
Mag-Stripe Credit Cards Weaknesses
- Weakness: the "secret" can be stolen along the whole path
- Call this "skimming" .. many forms
- e.g. a. in the magstripe reader ("skimmer")
- e.g. b. in the POS (Point of Sale) device
- - Target POS breach, 40 million cards
- e.g. c. the waiter covertly swipes it to get the secret
- e.g. d. along the path to the issuing bank
- A "skimmer" bad guy device attached to ATM, steals "secret"
- e.g. Krebs Skimmer Example
- Conclusion: sending the "secret" unencrypted is a terrible system
- There are many places the bad guys can get to it
EMV Chip on Card
- There's a chip on the card
- The chip has a secret "key" on it, coded at the bank
- EMV uses keys and encryption (below)
- Important strategy improvement: the secret key never leaves the chip
- If the retailer's equipment is compromised .. we're still fine!
How EMV Works
- Insert the card chip-side up into the terminal
- Leave the card inserted, so it can communicate
- Merchant creates a payment request, sends it into the card
- The chip in the card creates with its secret an encrypted "blob" request
- -e.g. imagine the card encrypts the request with the secret key
- Merchant sends the encrypted blob to the issuer to request payment
- The issuer has a copy of the secret to decrypt the request
- Key improvement: Encrypted blob is useless to the bad guys if intercepted
- The secret never leaves the chip
- The secret is what one needs to make encrypted blobs
- Avoid needing 100% security along the card-to-issuer path
- I estimate EMV is about 100x more secure than mag-stripe for this "swipe" case
- The request includes the CC number but not the needed CVV1

EMV - Contactless
- The little wireless-pay terminals
- There are based on EMV too
- Apple Pay, Google Pay, etc.
- Retain the key feature: data interception is harmless
EMV Card Shift
- Mag stripe: anyone holding the card can get the info off it
- -Bad guy makes a duplicate card, goes to Best Buy etc.
- EMV: only the chip in the card can make a valid request
- -Having the card briefly does not allow one to make a duplicate
- Therefore: the bad guys must steal the physical card
EMV Weakness 1 - Card Stolen
- Now the physical card itself is vital
- Bad guy could steal it from your wallet, go use it
- Some EMV cards require a PIN, guarding against the card-stolen case
- In the US, issuers are choosing to not do PIN
- My guess: skimming was a big problem, card-stolen is relatively rare
- US issuers may add PIN back, once people are used to EMV
EMV Weakness 2 - On The Internet
- Typing your CC number on a web site is CNP (Card Not Present)
- CNP is not getting the benefit of the EMV chip
- When Europe introduced EMV, CNP fraud went up!
- Like there's a pool of bad guys, and the need something to do
- There's possible solutions, but no great solution yet
- Maybe cell phones will supplant cards eventually
- Basic agency problem: the merchants eat the loss for CNP fraud
- -But the issuers control the tech .. lack motivation
- The issuers eat the fraud for "skimming" fraud
EMV Summary
- This is going to be a big improvement
- Makes the skimming (Target) case disappear
- There are weaknesses, but not fatal ones
- We might see PIN get rolled out in the USA eventually
- Next we need to solve the CNP "internet" case